A malicious campaign has taken advantage of seemingly harmless Android dropper apps on the Google Play Store to put users’ devices at risk using Banking Services Malware.
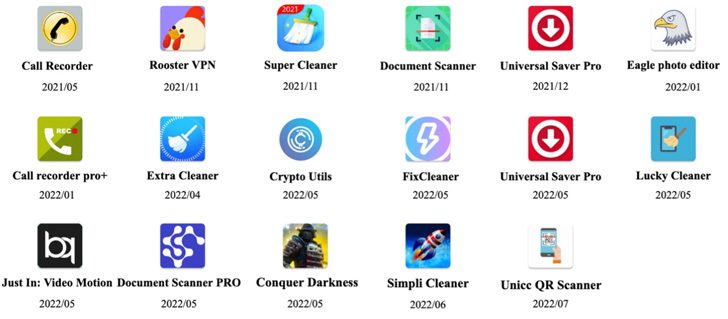
These 17 Dropper Apps, Dubbed Combined Daudruber By Trend Micro, disguised as productivity apps and utilities such as document scanners, QR code readers, VPN services, call recorders, and more. All these respective apps have been removed from the app market.
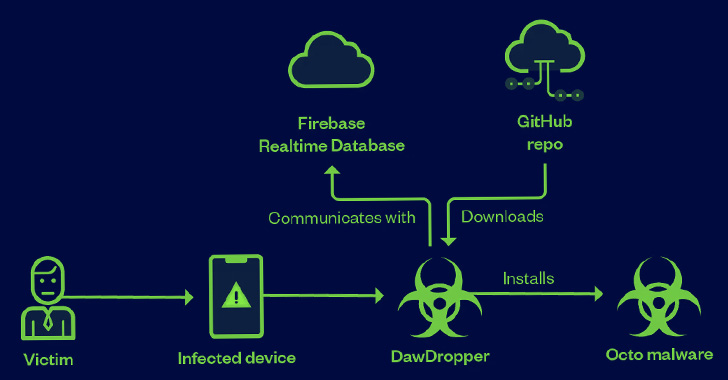
“DawDropper uses the Firebase Realtime database, a third-party cloud service, to avoid detection and dynamically obtain the payload download address,” the researchers said. He said. “It also hosts malicious payloads on GitHub.”
Droppers are apps designed to slip through Google Play Store security checks, after which they are used to download more powerful and intrusive malware onto the device, in this case, octo (cooper), hydraAnd the throw youAnd the thibot.
The attack chains included the DawDropper malware that establishes connections with the Firebase Realtime database to receive the GitHub URL needed to download the malicious APK file.
The list of malicious apps previously available from the App Store is below –
- Call Recorder APK (com.caduta.aisevsk)
- Rooster VPN (com.vpntool.androidweb)
- Super Cleaner – Hyper Smart (com.j2ca.callrecorder)
- Document Scanner – PDF Creator (com.codeword.docscann)
- Universal Saver Pro (com.virtualapps.universalsaver)
- Eagle Photo Editor (com.techmediapro.photoediting)
- call recorder pro + (com.chestudio.callrecorder)
- Extra Cleaner (com.casualplay.leadbro)
- Crypto Utils (com.utilsmycrypto.mainer)
- FixCleaner (com.cleaner.fixgate)
- Just In: Video Motion (com.olivia.openpuremind)
- com.myunique.sequencestore
- com.flowmysequto.yamer
- com.qaz.universaver
- Lucky Cleaner (com.luckyg.cleaner)
- Simpli Cleaner (com.scando.qukscanner)
- Unicc QR Scanner (com.qrdscannerratedx)
An app called “Unicc QR Scanner” is included among the trains that were previously Reported by Zscaler Earlier this month, the Coper Banking Trojan, a type of mobile malware from Exobot, was distributed.
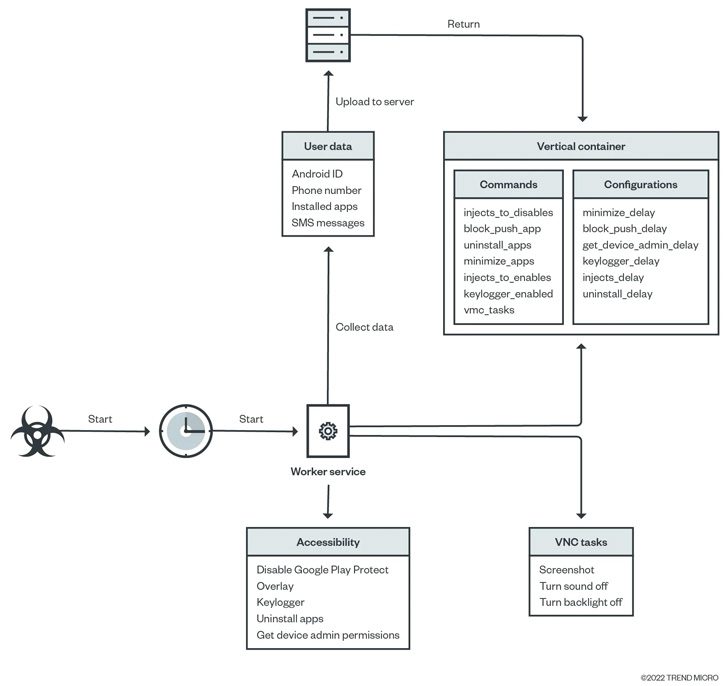
It is also known to disable Octo google play for protection and use Virtual Network Computing (VNC) to record a victim’s device screen, including sensitive information such as bank credentials, email addresses, passwords, and PINs, all of which are later leaked to a remote server.
For their part, the bank dropouts evolved Since the beginning of the year, it has moved away from encrypted payload download addresses with a middleware to mask the address that hosts the malware.
“Cybercriminals are constantly finding ways to avoid detection and infecting as many devices as possible,” the researchers said.
In addition, due to the high demand for new ways to distribute malware on mobile devices, many malicious actors claim that their mining tools can help other cybercriminals spread their malware on the Google Play Store, leading to the use of Dropper as a service (DaaS) Model.”

“Total alcohol fanatic. Coffee junkie. Amateur twitter evangelist. Wannabe zombie enthusiast.”







More Stories
Is this what the PS5 Pro will look like? (Image)
Finally, Windows 11 24H2 update significantly boosts AMD Ryzen – Windows 11 performance
Heart Surgeon Reveals The 4 Things He ‘Totally Avoids’ In His Life