

Getty Images
For over a decade, we’ve been receiving promises that a world without passwords is right around the corner, and yet, year after year, this security nirvana has proven elusive. Now, for the first time, a workable form of passwordless authentication is about to become available to the masses in the form of a standard adopted by Apple, Google, and Microsoft that allows pass keys across platforms and across services.
Pushed password-killing schemes in the past have had a host of problems. One of the main drawbacks was the lack of a viable recovery mechanism when someone lost control of the phone numbers or physical codes and phones associated with an account. Another limitation is that most solutions ultimately fail to be, in fact, truly passwordless. Instead, they gave users options to sign in with a face or fingerprint scan, but these systems eventually fell back to a password, meaning phishing, password reuse, and forgetting passcodes—all reasons we hated passwords to start with—why not Go away.
new approach
What’s different this time is that Apple, Google, and Microsoft all seem to be collaborating on the same well-defined solution. Not only that, but the solution is easier than ever for users, and it’s less expensive for big services like Github and Facebook. It has also been meticulously designed and reviewed by experts in authentication and security.
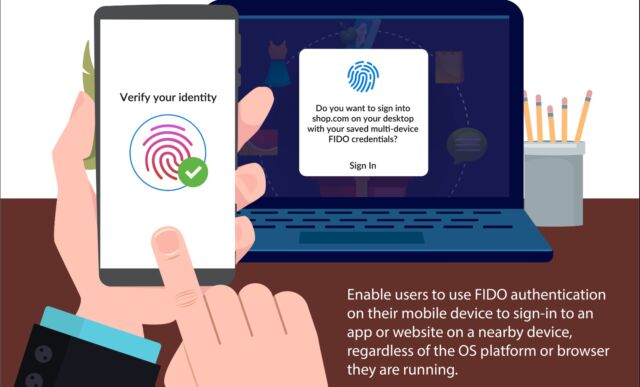
video alliance
Existing Multi-Factor Authentication (MFA) methods have made significant strides over the past five years. Google, for example, allows me to download an iOS or Android app that I use as a second factor when I sign into my Google account from a new device. Based on CTAP – short for Client for authenticator protocol—This system uses Bluetooth technology to ensure that the phone is close to the new device and that the new device is, in fact, connected to Google and not a site masquerading as Google. This means that it is incorruptible. The standard ensures that the encryption secret stored on the phone cannot be extracted.
Google also provides a file Advanced Protection Program Requires physical keys in the form of a standalone dongle or end user phones to authenticate logins from new devices.
The big limitation now is that passwordless authentication and MFA authentication are rolled out differently – if at all – by each service provider. Some providers, such as most banks and financial services, still send one-time passwords via SMS or email. Realizing that these are not safe means of transmitting security-sensitive secrets, many services have moved to a method known as TOTP, which is an acronym for One time password based on time– to allow a second factor to be added, which effectively increases the password by a factor of “something I have”.
Physical security keys and TOTPs, and to a lesser extent two-factor authentication through SMS and email are an important step forward, but three major limitations remain. First, TOTPs are generated through authentication applications and sent by text or email cheatable, the same way as regular passwords. Second, each service has its own closed MFA platform. This means that even when using non-separable forms of MFA – such as stand-alone physical keys or phone-based keys – the user needs a separate key for Google, Microsoft, and all other Internet properties. To make matters worse, each OS platform has different mechanisms for implementing the MFA.
These issues give way to a third problem: the sheer lack of use for most end users and the counterintuitive cost and complexity that each service encounters when trying to offer MFA.





More Stories
Is this what the PS5 Pro will look like? (Image)
Finally, Windows 11 24H2 update significantly boosts AMD Ryzen – Windows 11 performance
Heart Surgeon Reveals The 4 Things He ‘Totally Avoids’ In His Life